Since Windows XP Service Pack 2 was launched, every time you try to run or open a file that has been downloaded from the Internet, or more correctly, from the Internet Zone in Internet Explorer. You are prompted with the following warning message:
What this message does, basically, is to warn you that you are opening a file that is downloaded from an un-trusted location. You can see further evidence of this if you view the file’s properties:
Notice the Unblock button on the lower right. If you select it, the next time you try to open the same file you see no warning. Somehow, by pressing Unblock, you have told Windows that you want to allow this particular file, even if it is from the Internet. But where is this information stored? I searched in all the places I could think of; attributes, DACLs, SACLs, details. What prompted me to do this was that I wanted to unblock several file and was looking for a command line utility to do it. Not even Google knew where this information was stored.
The reason I wanted a command line tool was this. If you download an archive from the Internet and then extract the files in it before you unblock it, all the extracted files are also marked as coming from the Internet and require individual unblocking.
When I attended Tech Ed IT Forum last week in Barcelona I asked Microsoft Security Guru Steve Riley about this, and, not surprisingly, he knew the answer. The information is stored in an NTFS alternated data stream!
NTFS alternate data streams are a little known feature of the NTFS file system, and have been available since Windows NT 3.1. This feature allows you to store data of any kind in an alternate location within a file. When we use files normally we are accessing stream 0. When you open an EXE file or a DOC file you are reading stream 0 of that file. But as I said, you can add several more streams. A while back, ADSs was the cause of a security scare. Someone had read about ADS and found them to be a security risk. What if a malicious user stored a virus or malware in an ADS? The user and all his anti-virus and anti-malware software, would be oblivious! As it turned out, this quickly blew over and now several anti-virus/malware packages scan for the presence of ADSs within files.
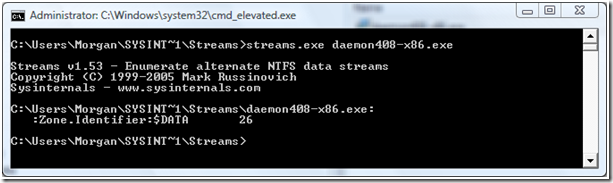
So how does this apply to files from the Internet? Consider this example; you have a file you have downloaded from the Internet. In my case it is called daemon408-x86.exe and is the installer for Daemon Tools. When I try to run this file I receive the warning mentioned earlier. Now that I know that this is caused by an alternate data stream I can use a tool to view and delete that stream. There are several tools available, but I chose streams from SysInternals. This is the output from streams for my file:
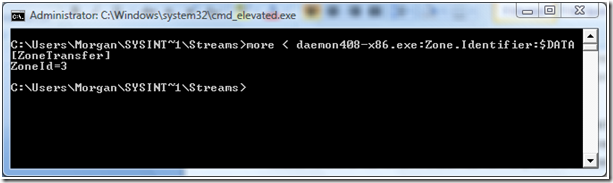
As you can see, this file has an ADS called Zone.Identifier:$DATA. To see what it contains we use the more command, which is part of Windows.
This is the raw data that is stored in the additional stream. Not very much in this case, just two lines of text. But this is what Explorer looks for when you ask to open a file.
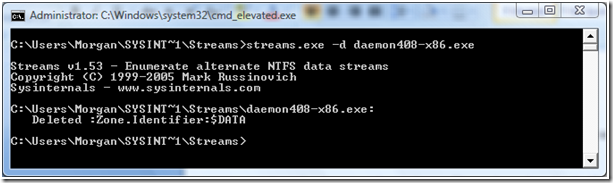
To delete this additional stream so that the file opens without warning we again use streams from SysInternals.
If you want to know more about NTFS Alternate Data Streams, check out these links:
- http://www.heysoft.de/nt/ntfs-ads.htm
- http://msdn.microsoft.com/library/default.asp?url=/library/en-us/dnfiles/html/ntfs5.asp
- http://support.microsoft.com/kb/105763
- http://www.diamondcs.com.au/index.php?page=archive&id=ntfs-streams
You can download the streams tool from the SysInternals site:
http://www.microsoft.com/technet/sysinternals/Utilities/Streams.mspx
Until next time!