Remote Desktop Connection (RDC) has a Group Policy setting that determines which publishers are to be considered trusted when launching connections (typically .rdp files served in various ways).
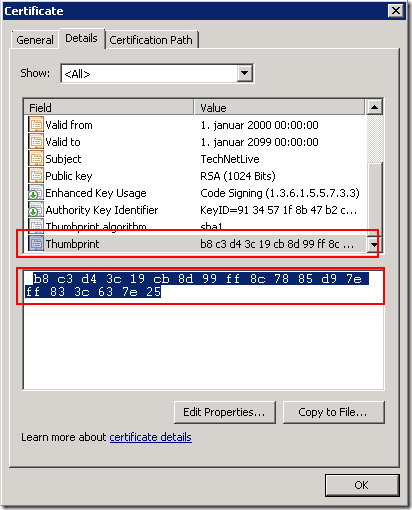
The publisher is identified by the SHA1 thumbprint of the certificate of the publisher (the certificate used to sign the .rdp file). You get the thumbprint from the certificate:
The setting is located under:
Computer Configuration\Policies\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Connection Client
Setting:
Specify SHA1 thumbprints of certificates representing trusted .rdp publishers
Description:
This policy setting allows you to specify a list of Secure Hash Algorithm 1 (SHA1) certificate thumbprints that represent trusted Remote Desktop Protocol (.rdp) file publishers.
If you enable this policy setting, any certificate with an SHA1 thumbprint that matches a thumbprint on the list is trusted. If a user tries to start an .rdp file that is signed by a trusted certificate, the user does not receive any warning messages when they start the file. To obtain the thumbprint, view the certificate details, and then click the Thumbprint field.
If you disable or do not configure this policy setting, no publisher is treated as a trusted .rdp publisher.
Notes:
You can define this policy setting in the Computer Configuration node or in the User Configuration node. If you configure this policy setting for the computer, the list of certificate thumbprints trusted for a user is a combination of the list defined for the computer and the list defined for the user.
This policy setting overrides the behavior of the “Allow .rdp files from valid publishers and user’s default .rdp settings” policy setting.
If the list contains a string that is not a certificate thumbprint, it is ignored.
As you can see; no mention of how the thumbprint is to be entered!
I found out the hard way that you have to remove all spaces and convert all letters to uppercase for the thumbprint to be valid. You are not informed if the format you enter is incorrect, it is just silently ignored if not recognized as a valid thumbprint.
This quick PowerShell command will do these two operations:
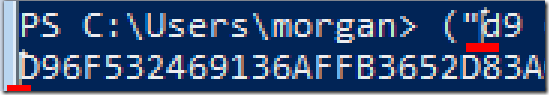
(“<your thumbprint here>”).ToUpper().Replace(” “,””)
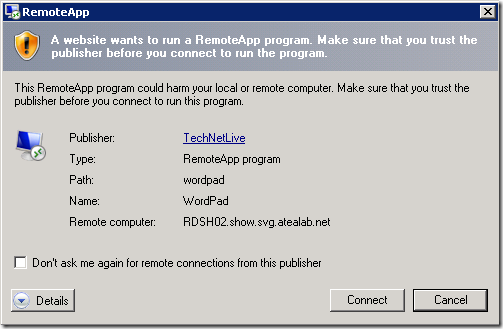
If this Group Policy setting is not in effect, either because you have not set it or the thumbprint is incorrect/invalid, your users will get a warning when connecting, even if the certificate used to sign the .rdp file is trusted:
Error: A website wants to run a RemoteApp program. Make sure that you trust the publisher before you connect to run the program.
It is interesting to note that the rdpsign.exe command line utility that is used to sign .rdp files manually, requires that the thumbprint of the certificate must be provided in just this way: http://technet.microsoft.com/en-us/library/cc753982(WS.10).aspx
More info:
- About Digitally Signing RemoteApp Programs:
http://technet.microsoft.com/en-us/library/cc754499.aspx
A note on copying the thumbprint
If you look at the highlighted/selected thumbprint in the image above you will see what looks like a leading whitespace. If you select the whole string (not as above), you will get a strange leading character in your thumbprint. Have a look at this zoomed image:
I do not know what character this is, but it invalidates the thumbprint string if you paste it into the SHA1 thumbprint field in your GPO. Even stranger is that it does not show up in the pasted text in the GPO object; it just “looks” right. As I said, I have no explanation, but remember to skip the leading whitespace when you copy your thumbprint.
This is how it should look: